- “The Cloud will cost x” (per user/month), but how much does my server actually cost me?
- For that matter, how much is all that data worth (to me)?
Author: Tom Gillies
Will losing constraints set you free?
- For many situations a constraint is redundant. The fundamental structure of many applications means they are unlikely to create orphan rows.
- The cost of the constraint is in the extra processing it causes during update operations. This cost is incurred every time a value in the constrained column is updated.
- The benefit of a constraint is that it absolutely protects the constrained column from rogue values. This may be particularly relevant if the system has components (such as load utilities or interfaces with other systems) which by-pass the normal business transactions.
- Other benefits of constraints are that they unequivocally state the “intention” of a relationship between tables and they allow diagramming tools which navigate the relationships to “do their thing”. Constraints provide good documentation, which is securely integrated with the database itself.
- The costs of constraints are small, but constant and in the immediate term.
- The benefits of constraints are avoiding a potentially large cost, but all in the future.
More Detailed Argument
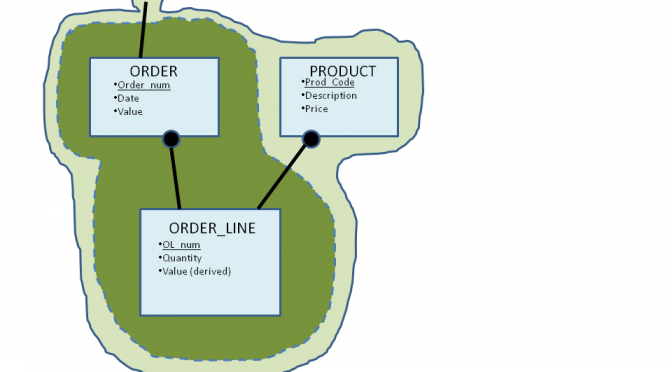
- we create or update the ORDER and ORDER_LINE entities, and
- in addition we refer to PRODUCT (to get availability and Price) and presumably to the CUSTOMER entity which isn’t shown on the diagram.
What if you don’t have a Data Model?
What’s the problem?
The method
- Preparation: Collect any documentation
- “Brainstorm:” Try to guess the tables/entities you will find in the database.
- List the actual Tables
- Group the Tables: based on name
- For each “chunk”, do the following:
- Identify “keys” for tables: Look for Unique indexes.
- Identify candidate relationships: Based on attribute names, and non-unique indexes.
- Draw your relationships.
- “Push out” any tables that don’t fit.
- Move on to the next group.
- When you’ve done all the groups, look for relationships from a table in one group to a table in another.
- Now try and bring in tables that were “pushed out”, or are in the “Miscellaneous” bucket.
- Repeat until you have accounted for all the tables.
The method stages in more detail.
Preparation:
“Brainstorm:”
List the tables:
Group the tables
Identify the candidate keys, and foreign keys from the indexes
From attribute names and indexes, identify relationships
- Sometimes the index names are a give-way (FK_…)
- Sometimes you have to look for similar column names (ORDER_LINE.ORDER_ID à ORDER.ID)
- Multi-part indexes sometimes indicate hierarchies.
Push Out
Look for “Inter.group” Relationships
How to “dig into a large database”?
I gave an answer in the forum, but here is an expansion, and some ponderings.
- Lots of tables
- Many terror-bytes 😉
- Lots of transactions
- Lots of users
- There may be other interpretations
I’m going to go with “Lots of tables” with the definition or “lots of” being:
I’ve also assumed that we are working with a “transactional database” rather than a “data warehouse”.
Preparation
- Understand objectives of “The Business”
- Understand the objectives of “This Project” (Digging into the Database)
- Collect relevant Organisation charts and find out who is responsible for doing what
- Collect relevant Process Models for the business processes which use the database
- Get hold of, generate, or otherwise create a data model (Entity Relationship Diagram or similar)
Of these, the one which is specific to working with a Database is the ERD. Having a diagram is an enormous help in visualising how the bits of the database interact.
Chunking
- Focus – on one chunk
- Prioritise – one chunk is more important, interesting or will be done before, another
- Estimate – chunks are different sizes
- Delegate – you do that chunk, I’ll do this one
- And generally “Manage” the work; do whatever are the project objectives.
I would use several techniques to divide the database or model up into chunks. These techniques work equally well with logical and physical data models. It can be quite a lot of work if you have a large model. None of the techniques are particularly complicated, but they are a little tricky to explain in words.
- Layering
- Group around Focal Entities
- Process Impact Groups
- Realigning
Organise the Data Model
- We take ORDERs from CUSTOMERs.
- Each ORDER consists of one or more ORDER_LINES and each line is for a PRODUCT.
- We Deliver what the customer wants as DELIVERY CONSIGNMENTS.
- Each CONSIGNMENT contains one or more Batches of product (I’ve haven’t got a snappy name for that).
- We know where to take the consignment by magic, because we don’t have an Address for the Customer!
- We reconcile quantities delivered against quantities ordered, because we sometimes have to split an order across several deliveries.
- That’s it!
Layering
- Classifications
- Things
- Transactions
- Reconciliations
Things
- People
- Organisations
- Products
- Places
- Organisation Units (within our organisation, or somebody elses)
Classifications
Transactions
- Order
- Delivery
- Booking
Reconciliations
Groups around Focal Entities
- “Customer and associated classifications” and
- “Order and Order_line” are candidate groups.
Process Impact Groups
- Select a business process
- Draw lines around the entities which it: creates, updates and refers to as part of doing its work.
- You should get a sort of contour map on the data model.
- Place Order
- Assemble Delivery Consignment
- Confirm Delivery (has taken place)
Realigning
Finally, “Chunking”
- combine neighbouring chunks together or
- you can use the techniques (especially “Focal entities” and “Process Entity Groups”) to break them down until you reach a single table/entity.
Tools
Security – Using Server Side security with MS SQL Server
- How does Server-side security work on MS SQL Server? And
- How can I control the access different users have to my database?
I’m not (have never been, and do not really intend to become) a DBA (Database Administrator). I understand a bit about “privileges” but in the past I’ve always had someone else “doing it for me”, and in any case , I’ve worked on other databases such as DB/2 or Oracle.
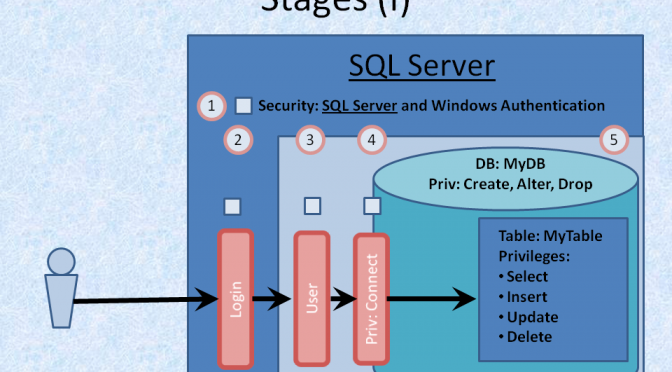
- A LOGIN, which gives access to the Server Instance, and with Server-side authentication, provides the security, and
- A USER, which belongs to the Database and is granted the Database privileges (including CONNECT).
- Ensure that SQL Server is set up to allow Server Authentication
- Create the LOGIN (in the SQL Server Instance)
- Create a USER corresponding with the LOGIN (in the Database)
- Grant the USER CONNECT privilege (happens by default, but can be revoked)
- Grant the USER the appropriate privileges on the Database